Password security has become a more pressing issue due to the rise of cloud technologies. Now, many companies have their data in cloud storage protected by two factor authentication and platforms like Microsoft 365, and hackers see a stolen or hacked login as the easiest way in.
According to Verizon’s 2020 Data Breach Investigations Report (DBIR), password dumpers have become the number one malware used in data breaches, and password theft has surpassed all other objectives in phishing emails.
Cybercriminals are finding that getting past the security of a large cloud vendors like Amazon, Google, or Microsoft is much more difficult than just stealing user credentials to gain access.
These days, cloud solutions need to be part of any Brisbane company’s cybersecurity strategy, which includes both proper security configurations in cloud platforms and strong password security.
One of the best ways to protect logins is through two-factor authentication (2FA). According to Microsoft, whose cloud services see about 300 million fraudulent sign-in attempts per day, 2FA can block 99.9% of those unauthorised sign-ins.
How Two Factor Authentication Works
The most common form of two factor authentication uses two methods of confirming a user is legitimate:
- The username and password combination
- A time-sensitive code sent to a device in the possession of the user
These two factor codes are called, “what you know” and “what you have.”
2FA is so successful at blocking malicious sign-in attempts because the hacker doesn’t typically have possession of the device that receives the 2FA code, so they can’t complete the login.
But are all forms of 2FA the same? Not quite. There are differences in security when it comes to the way you receive the login code.
Security Breakdown of the Different Forms of 2FA
When you implement two factor codes to improve your cybersecurity, there are typically three different options for receiving that 2FA code that’s input at login.
These are:
- Receive it by text message (SMS) to your mobile phone
- Receive it through a 2FA authentication app with on-device prompt
- Receive it through a special security key that you plug into your device
We’ll go through each method below, beginning with the least secure and moving to the most secure of the three methods.
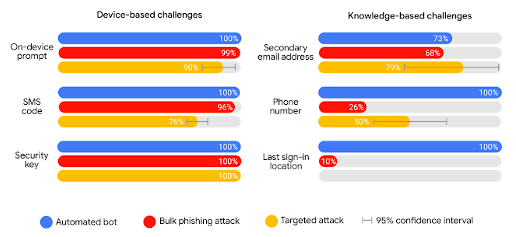
Google Study on Authentication Methods
Receiving via Text/SMS
By far, the most common method for receiving security codes is via SMS. The user is asked when registering for a mobile phone number that should be used and receives a confirmation code to input to ensure they have that device in their possession.
Each time the user logs in, they receive a text with a time-sensitive code to input. According to a Google study, this is how receiving the 2FA code via SMS performs
Each time the user logs in, they receive a text with a time-sensitive code to input.
According to a Google study, this is how receiving the 2FA code via SMS performs:
- Blocks 100% of automated bot attacks
- Blocks 96% of bulk phishing attacks
- Blocks 76% of targeted attacks
Some of the security concerns with receiving a code via SMS is that sim cards can be cloned by criminals, which would give a hacker access to a user’s text messages, and thus to their two step verification codes. The SMS also generally says who it’s from, so it would be easy for a criminal to identify the website that sent the code and target that for a hack.
On-Device Prompt of Authentication App
A slightly more secure method of receiving the two step verification code is through an authentication app on a smartphone or other device that will give an on-device prompt with the sign-in code.
This is commonly used with iCloud sign-ins through a native app. One of the most popular authenticator apps is Google Authenticator.
This method of receiving the two factor codes scored the following in the Google study:
- Blocks 100% of automated bot attacks
- Blocks 99% of bulk phishing attacks
- Blocks 90% of targeted attacks
It’s more secure than SMS, but not quite as “airtight” as a security key.
One of the security issues with an on-device prompt through an app is that if a thief has stolen a smartphone, tablet, or laptop with that authenticator app installed, they have access to the 2FA codes to break into user accounts.
Security Key Verification
The most secure form of two step verification is through a separate security key device. This is typically more expensive than the other two methods (which are often free), but it offers the highest level of protection for login security.
Users purchase the security key from a company like Yubico (YubiKey) or Thetis (Fido). The key is a small device about the size of a USB drive or smaller. It’s physically plugged into a computer or mobile device to complete a login that uses two step verification.
Because this device can’t be cloned like a sim card and the hacker would need to physically steal that small device from a user to gain access, it’s considered the most secure of any of the three forms.
Here’s how using a security key rated in the Google study:
- Blocks 100% of automated bot attacks
- Blocks 100% of bulk phishing attacks
- Blocks 100% of targeted attacks
Is Your Cloud Data Properly Protected?
Are you looking at improving your cybersecurity methods via a two factor authentication code? Connected Platforms can help with your cloud solutions for small business by putting strong password solutions in place that ensure your accounts are protected. Contact us for a free consultation by calling (07) 3062 6932 or book a coffee meeting online.




