Ransomware Malware is a constant concern for any size business. Just one attack can halt operations by making data inaccessible, costing companies hundreds of thousands of dollars in downtime costs.
One of the more recent attacks in Australia was against beverage company Lion, who confirmed in June two ransomware attacks on its systems (the second coming as they were trying to deal with the first).
The firm had to shut down its IT systems, which reduced its manufacturing capabilities and the ability for customers to place orders.
Ransomware is one of the costliest types of malware that can infect your network via things like phishing attacks, malicious URLs that do “drive-by” downloads, and infected USB drives.
Costs associated with a ransomware attack include:
- IT disaster recovery
- Downtime costs
- Lost opportunity costs
- Employee productivity costs
- Reputation damage
According to the Sophos “The State of Ransomware 2020” report, Australia pays the third highest ransomware remediation costs in the world at an average of US$1,122,914 (AUD$1,550,943) per incident.
The report also found that if the ransom was paid, those costs nearly double.
48% of Australian organisations were hit with ransomware within the last year.
The amount that you end up paying in remediation costs can vary widely according to factors such as whether or not you pay the ransom, whether you have a reliable backup and recovery plan in place, and how you react in the first minutes and hours after a ransomware malware attack has occurred.
Mitigate Losses by Taking the Right Steps Immediately After a Ransomware Malware Attack
When you walk into your office and find a ransomware popup on your computer, it can send you and your team into panic mode.
This example below is from Wikipedia and shows a message related to the WannaCry ransomware infection. The typical ransom currently being requested is much higher, in the thousands of dollars.
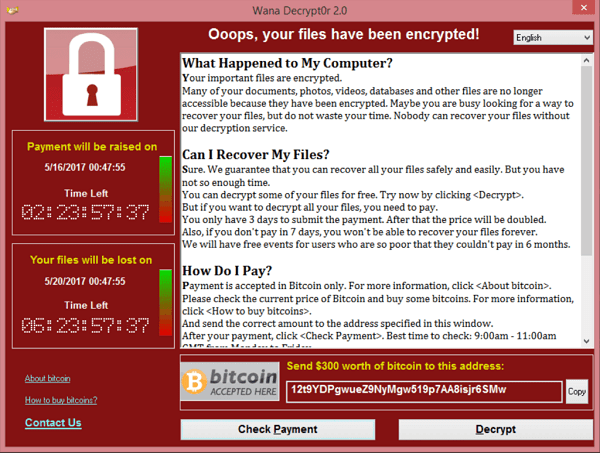
Before you try removing the malware yourself (which could lead to permanent loss of files), take the following steps to mitigate your losses and help contain the infection as soon as possible.
Use Your Phone to Take a Photo of the Ransom Demand
Anything could happen when it comes to ransomware, and you don’t want to lose valuable information due to a power outage turning off your device. The very first thing you want to do is quickly snap a photo of the ransom demand that has appeared on your screen.
While you take the additional steps below, you could have someone send that image to your technology service professional, which will help them identify exactly what type of ransomware you’ve been hit with.
Not all ransomware strains are the same. Some will actually encrypt files on your hard drive, requiring a key to decrypt them. While others won’t encrypt them, they’ll just put up roadblocks to keep you from getting to your data.
Some ransomware malware also includes trojan programs that come along for the ride and can seek out things like login details to cloud accounts or online banking.
Disconnect Your Internet and Local Area Network (LAN)
If the note has popped up on just one device, that doesn’t mean that other devices aren’t also in the process of being infected. So, you want to not only disconnect the infected device from the internet and any LAN, you want to disconnect all devices on the network in case they may also be infected.
The fastest way to cut off your office-wide internet connection is to unplug your modem. You’ll also want to ensure that devices inside your office can’t connect to each other using an internal network or LAN.
Ransomware is designed to spread rapidly to other devices and cloud accounts, so you want to stop those connections as fast as possible.
Have Your IT Provider Evaluate the Extent of the Damage
You’ll want to bring in a professional to help you evaluate the extent of the damage. This will include evaluating the device with the ransom demand on the screen and looking at all other devices on your network to see if any others also have the ransomware on their drives.
Using a clean device, your IT provider will also review any cloud accounts that may have been syncing to infected devices (like OneDrive or Dropbox) to see if they were also impacted by the ransomware.
We will also find out what data may have been compromised by the ransomware (login credentials, etc.) based upon the type it is and by reviewing system details.
Removal and Replacement (or Ransom Payment)
In most cases, you do not want to pay the ransom. If you do, you have no guarantee that you’ll actually get access to your data back. Paying the ransom also just encourages the attackers to keep on attacking for a payoff.
In this regard, Australians are one of the best positioned, only 12% of Australian businesses pay a ransomware attacker, according to the Sophos report.
This step is where having a good backup and recovery system in place is essential. If you’ve been backing up all your data as you should, then your IT professional can safely remove the ransomware from any infected devices and restore the clean data in a fairly short amount of time.
If you don’t have a full backup of your files, then any type of restoration may take longer and may not be complete.
Put a Strong Backup and Disaster Recovery Strategy in Place
Connected Platforms can help your business be prepared in the case of a ransomware malware attack or any other data loss incident.
Contact us today for a free consultation. Call (07) 3062 6932 or book a coffee meeting online.




